ewtnet.com > How To Configure Java Phones Using Opera Mini 5 2
It might interest you to know that you can now configure your java phones using the latest opera mini 5.2 free. examples of java phones are: Nokia C1. Nokia C2,…
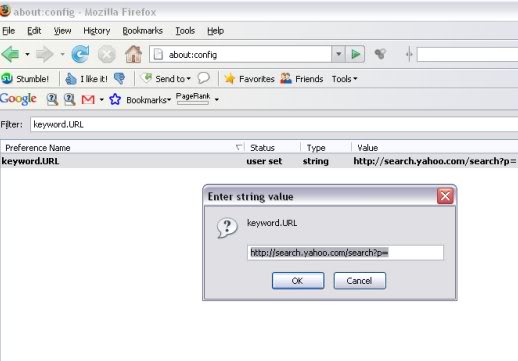
ewtnet.com > How To Configure Firefox Address Bar With Search Engines
Your Firefox address bar can not only be used for opening websites but also for searching as well. Yes, you can configure the Firefox address bar with various search engines…
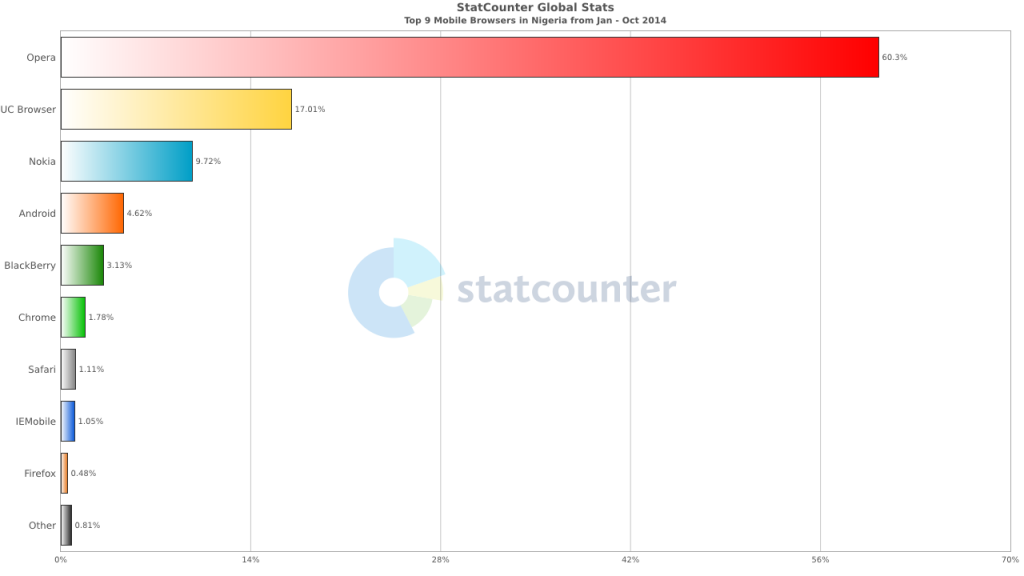
ewtnet.com > How To Use And Configure Wi Fi Hotspot
If you don't have a home internet access, your best bet is to use your Android smartphone to distribute your cellular Internet connection to your other devices. Using our guidelines…
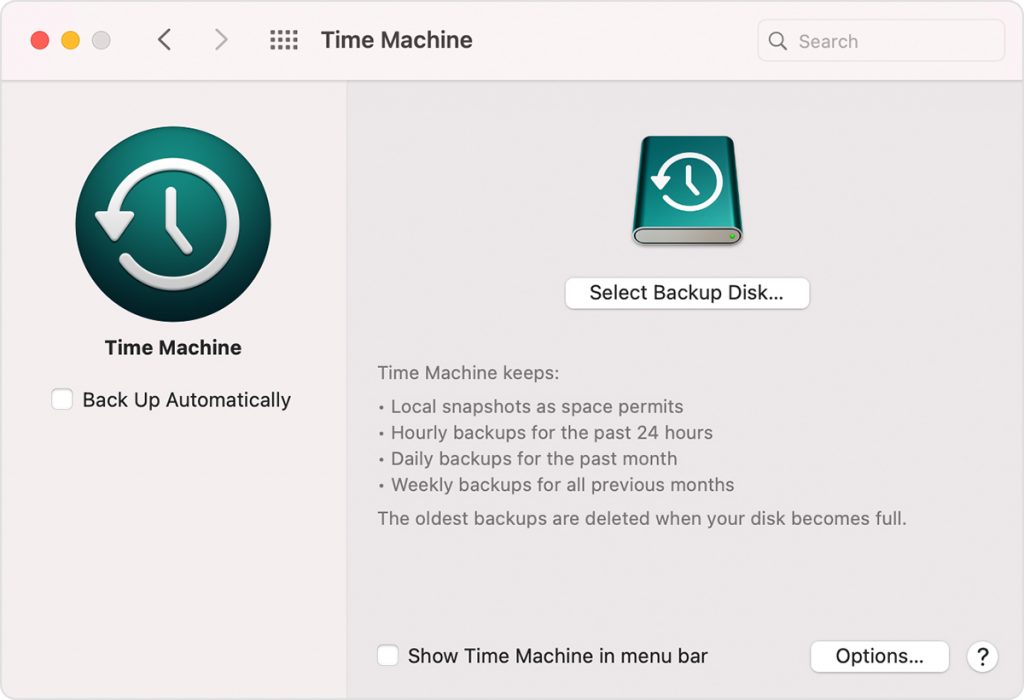
ewtnet.com > Backup Mac Time Machine
Creating a backup of your Mac is the only guarantee you can have of never losing your data and Apple has made it incredibly easier for you with Time Machine.…
ewtnet.com > Highest Paying Tech Jobs
The tech industry continues to be a driving force in the global economy, with demand for skilled professionals skyrocketing. This demand for specialized skills in this sector has never been…
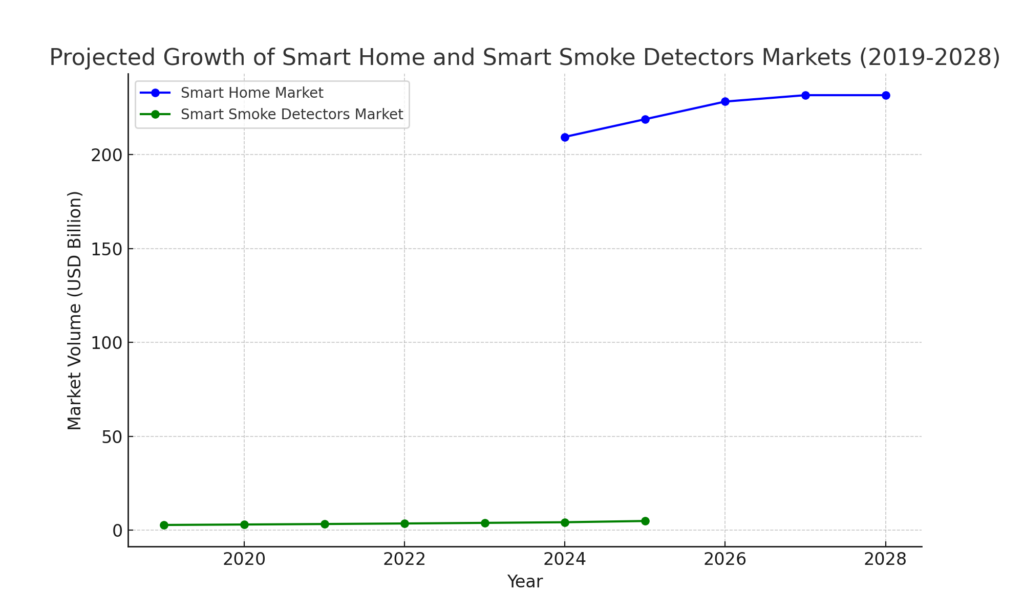
ewtnet.com > Best Smart Smoke Alarm For Modern Homes
Say goodbye to old, clunky smoke detectors that clash with your home decor. Smart smoke alarms are here, combining sleek designs with cutting-edge technology to fit seamlessly into any home…
ewtnet.com > Smart Smoke Alarms For Modern Homes
Gone are the days of clunky, obtrusive smoke detectors that clash with your home decor. Smart smoke alarms—the latest in home technology—come in sleek, modern designs that easily blend with…
ewtnet.com > Best Budget Android Phones To Buy In 2024
There have been mindblowing changes lately to Android phones thanks to some seriously powerful new chips. Remember when you had to pick between shelling out big bucks for a best-value…
ewtnet.com > Understanding The Role Of Cloud Access Security Brokers In Data Protection
CASBs are standard tools that offer several layers of protection for your organization. These include malware prevention, which ensures ransomware and other advanced persistent threats cannot access data on disk…
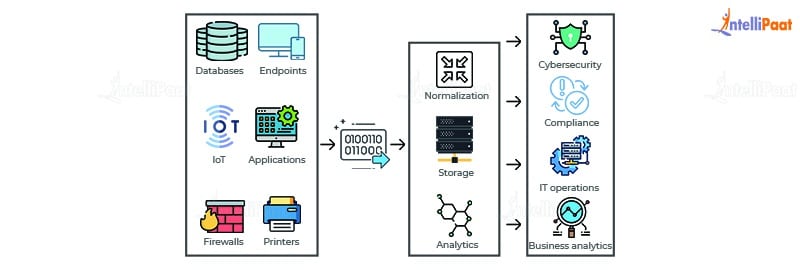
ewtnet.com > Key Benefits Of Implementing An Siem System
Security Information and Event Management, popularly known as SIEM system, is critical to any cybersecurity strategy. It helps protect against threats and provides visibility into your entire IT environment. SIEM…