Articles found for Compromised
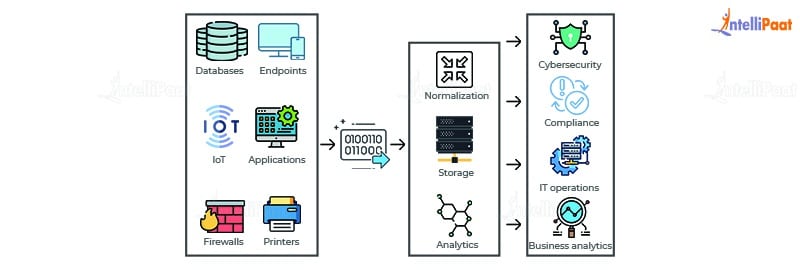
Understanding the Role of Cloud Access Security Brokers in Data Protection
CASBs are standard tools that offer several layers of protection for your organization. These include malware prevention, which ensures ransomware and other advanced persistent threats cannot access data on disk…
Apple device IDs hacked: What you need to know
A hacker collective known as AntiSec has published over a million Apple device IDs that it claims were captured from the laptop of an FBI agent. If you own an…
Your PC may come with malware pre-installed
It is rare to find a new PC that doesn’t come with additional bells and whistles in addition to the operating system itself. The “bloatware” that PC vendors add on…